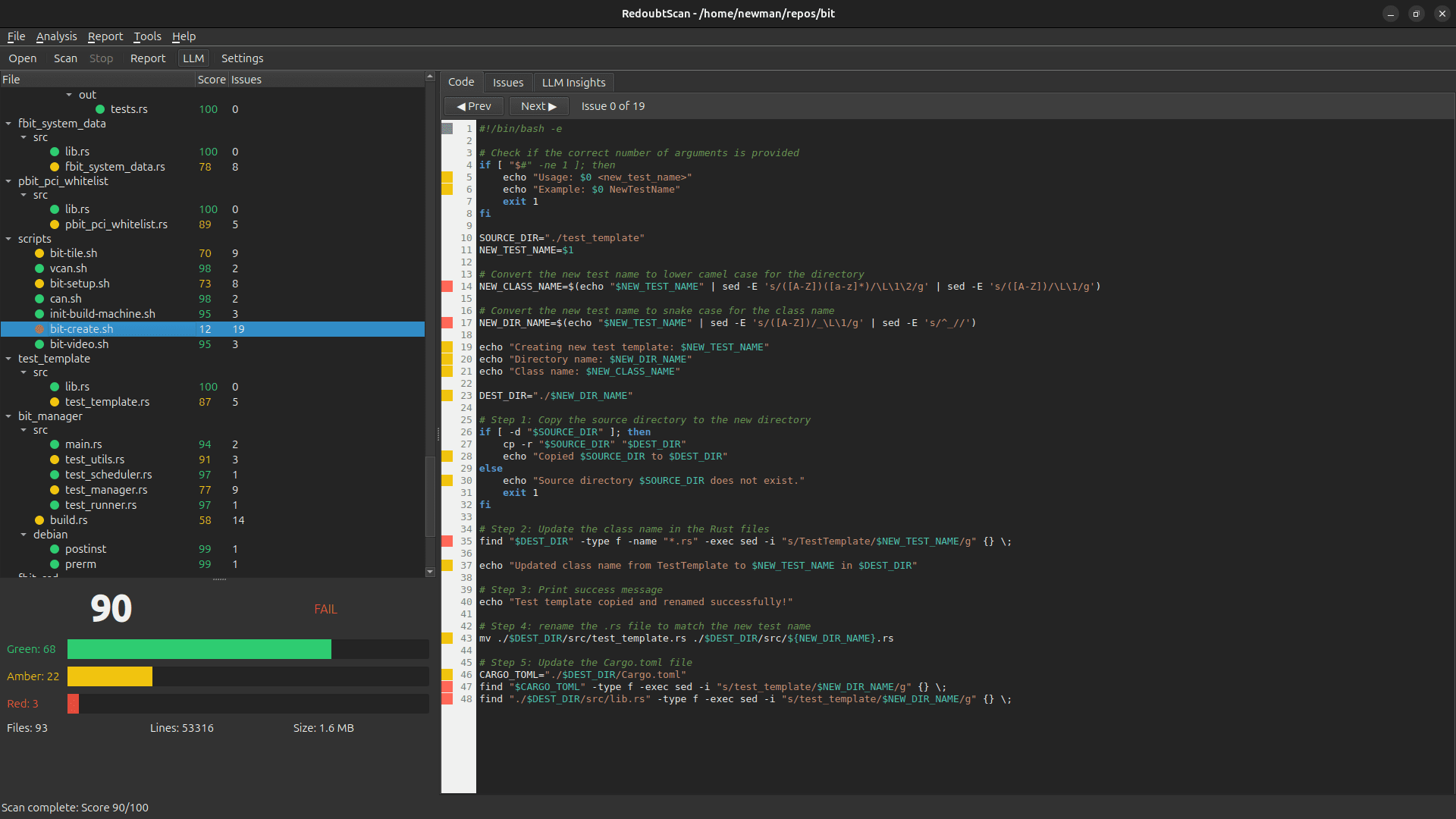
How RedoubtScan brings enterprise-grade code security to air-gapped environments
In an era where software supply chain attacks have become the weapon of choice for sophisticated threat actors, organizations face an uncomfortable truth: the code you didn’t write is often your greatest vulnerability. Third-party libraries, open-source dependencies, and vendor-supplied components form the backbone of modern applications yet they remain largely opaque to traditional security processes.
At Astute Systems, we built RedoubtScan to address this challenge head-on, and we did it with AI at every level of the stack.
The Problem: Trust, But Verify
When your development team pulls in a new library or updates an existing dependency, how confident are you in that code? npm, PyPI, crates.io, and Maven Central collectively serve billions of package downloads monthly. Each one represents a potential entry point for:
Supply chain compromises – Malicious code injected into legitimate packages
Dormant vulnerabilities – Security flaws waiting to be discovered and exploited
Code quality issues – Memory leaks, race conditions, and logic errors that degrade reliability
Compliance violations – Licensing conflicts or regulatory non-compliance
Traditional approaches rely on CVE databases and signature-based scanning. But what about the vulnerabilities that haven’t been catalogued yet? What about the subtle logic flaws that automated tools miss?
Enter RedoubtScan: AI-Powered Code Auditing
RedoubtScan is a Qt6-based code audit tool that combines pattern-based static analysis with local Large Language Model (LLM) assessment. But what makes it unique is its commitment to offline-first operation.
Why Offline Matters
In sensitive environments—defence contractors, financial institutions, healthcare providers, critical infrastructure operators—sending source code to cloud-based analysis services isn’t just inconvenient, it’s often prohibited. Air-gapped networks exist for good reason.
RedoubtScan runs entirely on your infrastructure:
No cloud dependencies – Your code never leaves your network
Embedded LLM support – Built-in llama.cpp integration for serverless AI inference
Local model hosting – Support for Ollama and self-hosted OpenAI-compatible endpoints
Offline licence validation – Even licensing works without internet connectivity
AI Inside: Multi-Layer Analysis
Our analysis pipeline leverages AI at multiple stages:
Pattern Recognition – Traditional regex and AST-based scanning for known vulnerability patterns across Python, Bash, C, C++, Java, and Rust
Static Analysis Integration – Orchestration of industry-standard tools like Bandit, ShellCheck, cppcheck, and Clippy
LLM-Powered Assessment – Deep semantic analysis using local language models to identify:
– Context-dependent vulnerabilities
– Business logic flaws
– Insecure design patterns
– Documentation gaps and maintainability issues
- Intelligent Scoring – AI-assisted risk scoring with our Green/Amber/Red traffic light system, making results actionable for both developers and executives
AI Outside: Built With Modern Tooling
RedoubtScan itself was developed using AI-assisted workflows. From initial architecture to code generation to documentation, we practised what we preach. The result is a codebase that’s:
– Well-structured and maintainable
– Thoroughly documented
– Consistent in style and patterns
– Designed for extensibility
Real-World Use Cases
Continuous Third-Party Validation
Scenario: A defence contractor receives quarterly software updates from a vendor. Before deployment, every update must be validated against security requirements.
Solution: RedoubtScan scans the entire codebase, generating comprehensive PDF and HTML reports. Results are tracked over time, with the caching system ensuring only changed files are re-analysed. Teams can quickly identify:
– New vulnerabilities introduced in the update
– Previously flagged issues that remain unresolved
– Overall security posture trends
Open Source Due Diligence
Scenario: An enterprise is evaluating an open-source library for inclusion in their product. They need to understand the security implications before committing.
Solution: Point RedoubtScan at the repository. Within minutes, receive a detailed breakdown of potential issues, code quality metrics, and an overall risk assessment. The LLM analysis provides context that pure signature-based tools miss—like identifying that a particular code pattern, while not technically vulnerable, represents a maintenance burden likely to introduce bugs over time.
Pre-Merge Security Gates
Scenario: A development team wants to catch security issues before they land in the main branch.
Solution: Integrate redoubtscan-cli into CI/CD pipelines. Use threshold flags to fail builds that don’t meet security standards:
redoubtscan-cli /path/to/code --fail-on-red --threshold 70 -f json -o report.json
The –fail-on-amber flag provides stricter enforcement for high-security projects.
Audit Trail and Compliance
Scenario: Regulatory requirements mandate regular security assessments with documented evidence.
Solution: Schedule periodic scans with report generation. RedoubtScan’s caching ensures efficient re-analysis, while comprehensive PDF reports provide auditor-ready documentation. The Green/Amber/Red scoring system translates technical findings into executive-friendly metrics.
The Technology Stack
RedoubtScan is built on a foundation of proven technologies:
– Qt6 – Cross-platform UI with native look and feel
– llama.cpp – Industry-leading local LLM inference
– Multiple scanner backends – Bandit, ShellCheck, cppcheck, Clippy, and more
– Flexible reporting – JSON, HTML, and PDF output formats
The architecture separates concerns cleanly:
– Core library – Scanning, analysis, and scoring logic
– GUI application – Full-featured desktop interface
– CLI tool – Automation and CI/CD integration
– LLM subsystem – Pluggable backends for different deployment scenarios
Getting Started
RedoubtScan requires a valid licence for operation. Licence files can be placed in standard locations:
/usr/local/share/astutesystems/license.json$HOME/astutesystems/license.json
Or specified via command line (–licence) or environment variable (GVA_LICENCE_PATH).
For organisations interested in evaluating RedoubtScan for their security workflows, contact us at [email protected] or visit astutesys.com.
Conclusion
Security isn’t a feature you bolt on at the end—it’s a practice you embed throughout. RedoubtScan embodies this philosophy, using AI to analyse code while being built with AI-assisted development practices.
In a world where your code is only as secure as your weakest dependency, having an offline-capable, AI-powered code auditor isn’t a luxury. It’s a necessity.
We are AI inside and out. And we’re here to help you secure what matters.
*RedoubtScan is developed by Astute Systems PTY LTD. For more information, visit https://astutesys.com