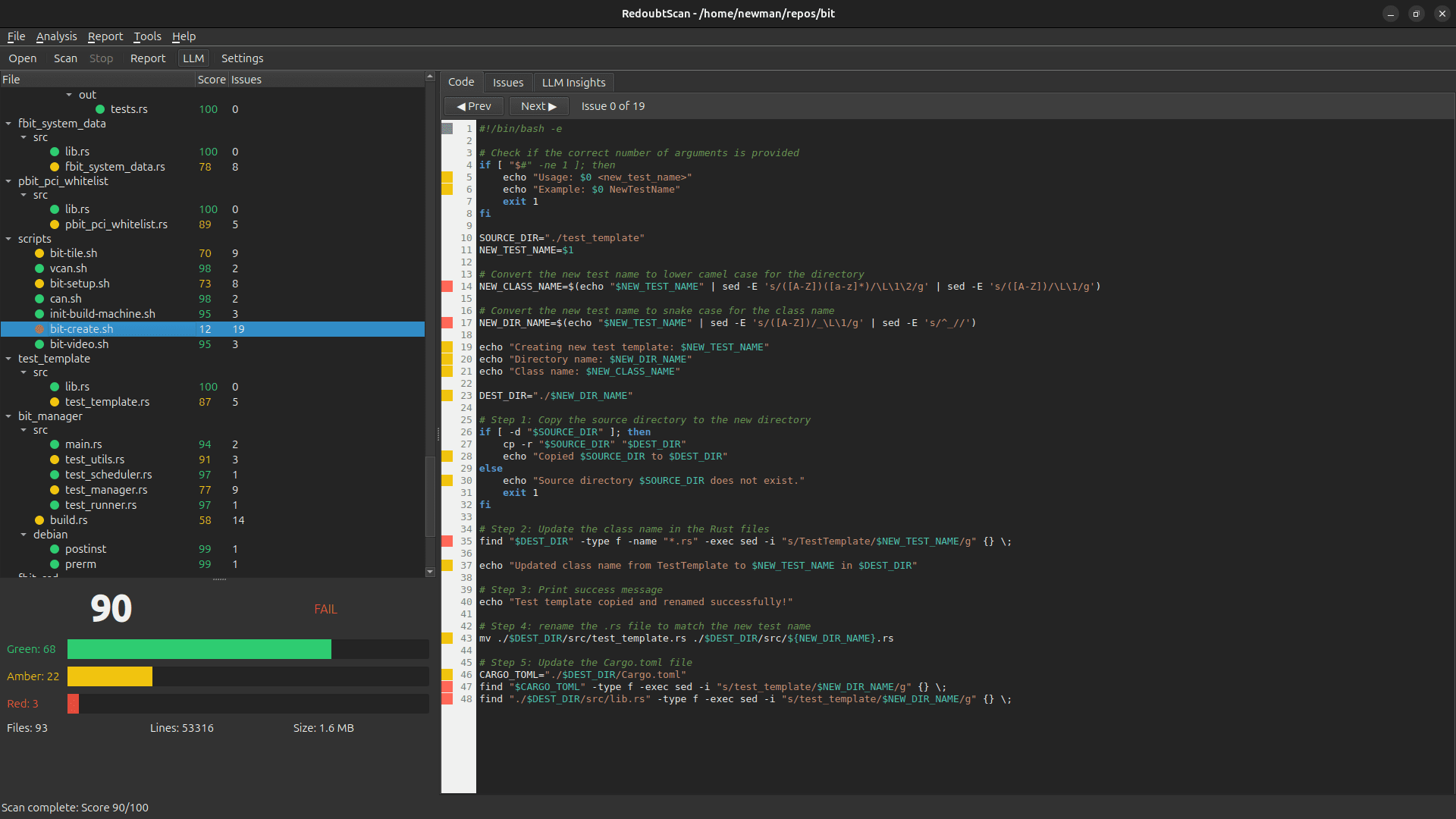
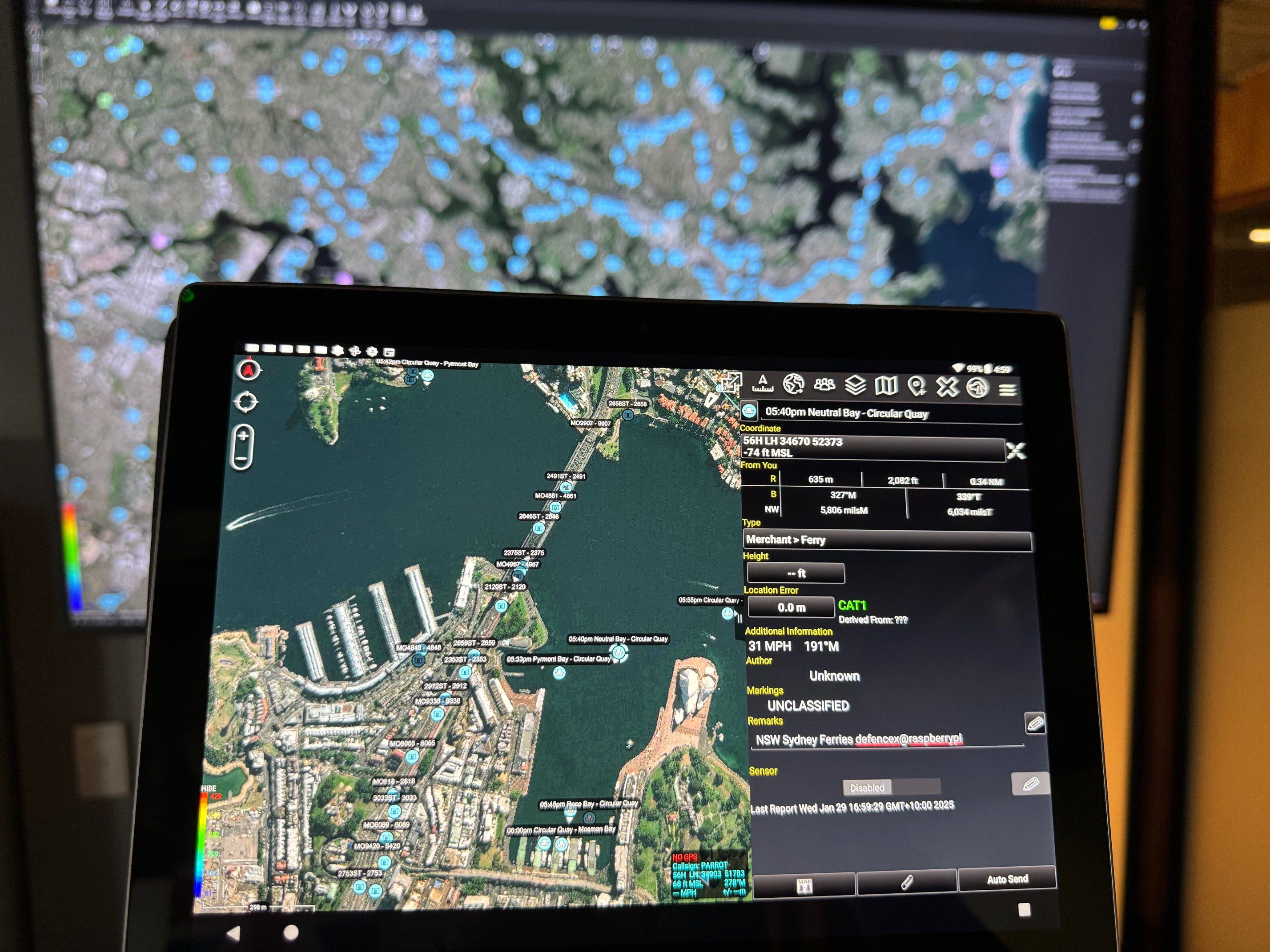
The Shifting Landscape of Defence Computing For decades, Intel x86 processors have been the default choice for defence computing platforms — from mission computers in armoured vehicles to command-and-control systems. That era is ending. The demands o...